The Invisible Supply Chain
If a Vendor in Your Supply Chain is Breached, Are You Exposed?
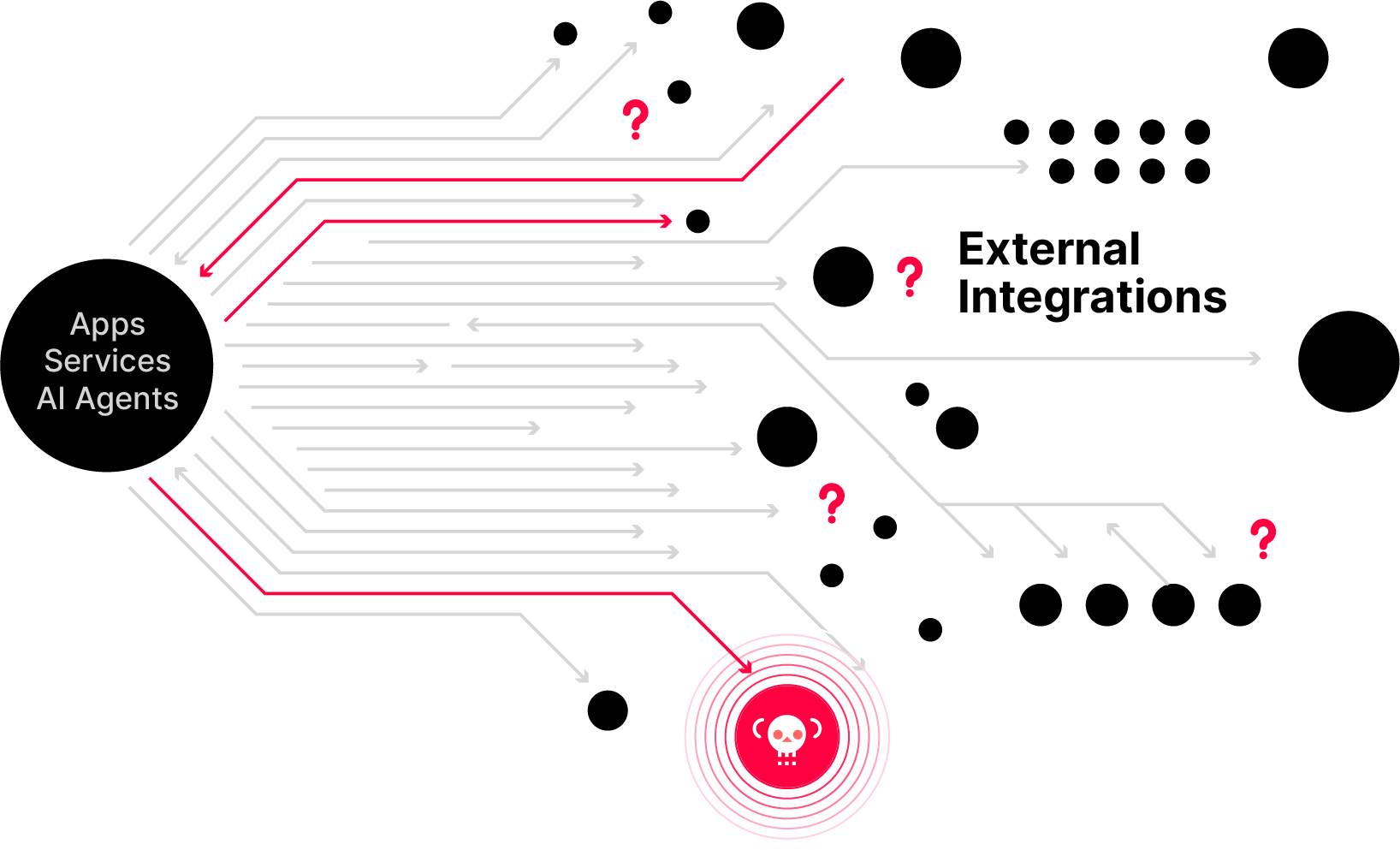
You can't answer that question because you don't know what data you're sending them. Modern applications rely on a complex web of third-party APIs, but since the traffic is encrypted, you're blind to the risk.
Key Pains
Unknown Connections
You can't produce a complete, real-time inventory of every third-party service your applications connect to.
Invisible Data
You have no idea if PII, credentials, or other sensitive data is being sent to vendors.
Manual Investigations
When a vendor announces a breach, it takes days or weeks of manual effort to determine your exposure.
From Blind Spot to Certainty
See Every Connection. Classify Every Payload.
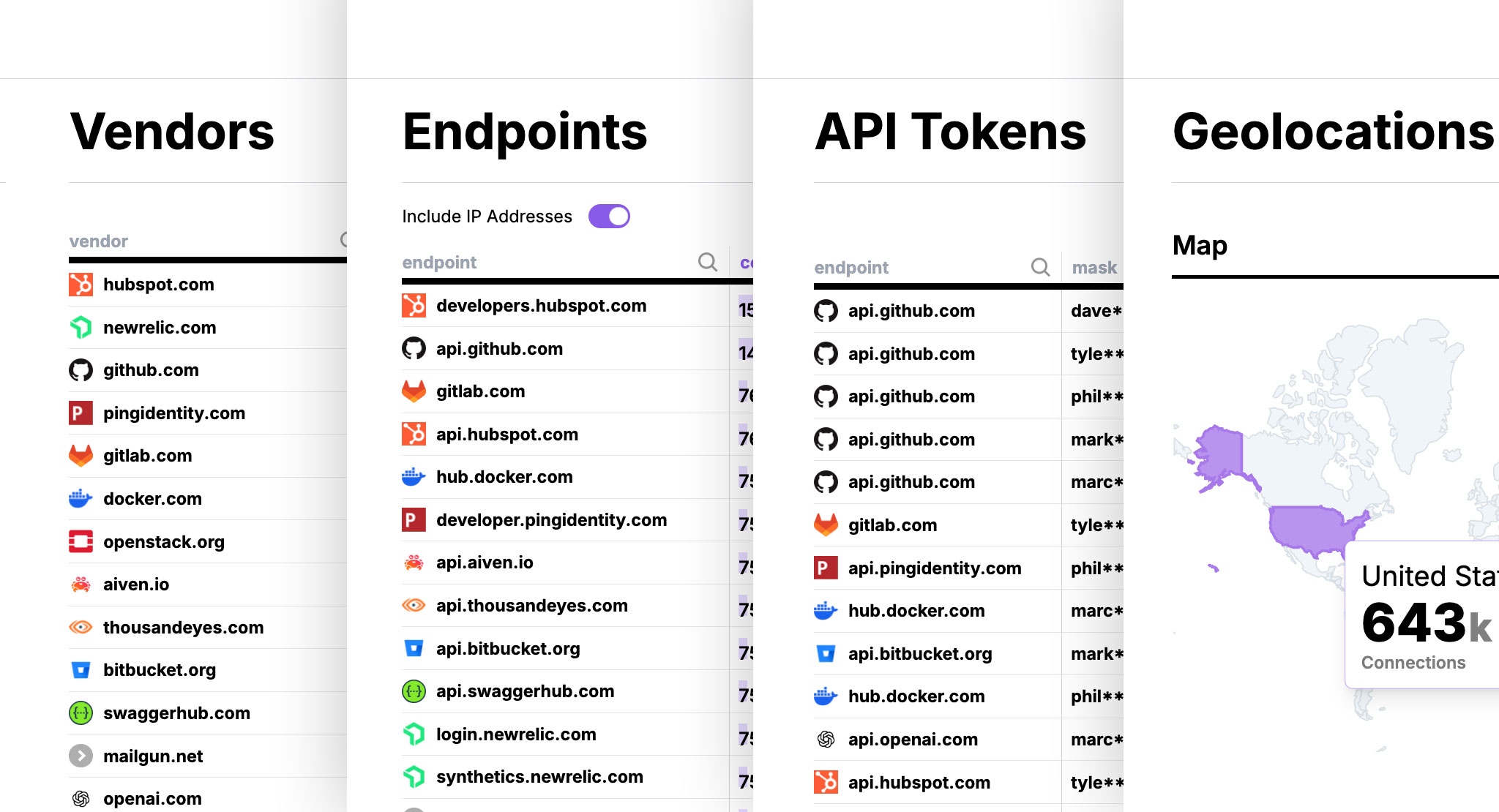
Qpoint provides the ground truth for your third-party data risk by observing traffic directly from the Linux kernel, bypassing encryption to give you a complete and immediate inventory.
Key Capabilities
Discover Every Connection
Instantly generate a real-time map of every external service your backend communicates with.
Classify Sensitive Data
Automatically scan payloads to detect and classify PII, PCI, PHI, and other sensitive data patterns.
Quantify Your Risk
Prioritize threats based on actual data exposure, not just guesswork.
Accelerate Incident Response
Get an immediate, definitive answer on your exposure during a third-party breach.
