How it works
From Zero to Visibility in Minutes

1.
Deploy With Zero Disruption
Install with a single command. No sidecars, no proxies, no code changes.
2.
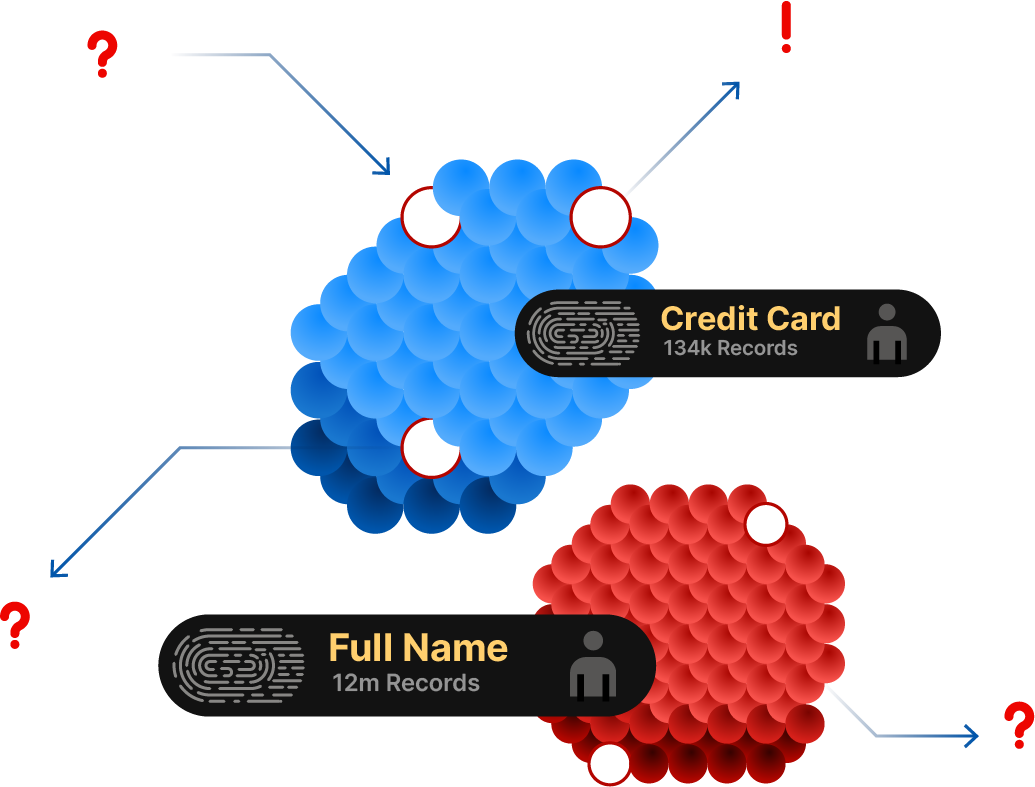
Automatically Discover & Classify
Instantly discover every connection and use ML to classify sensitive data (PII, secrets) in the payload.
3.
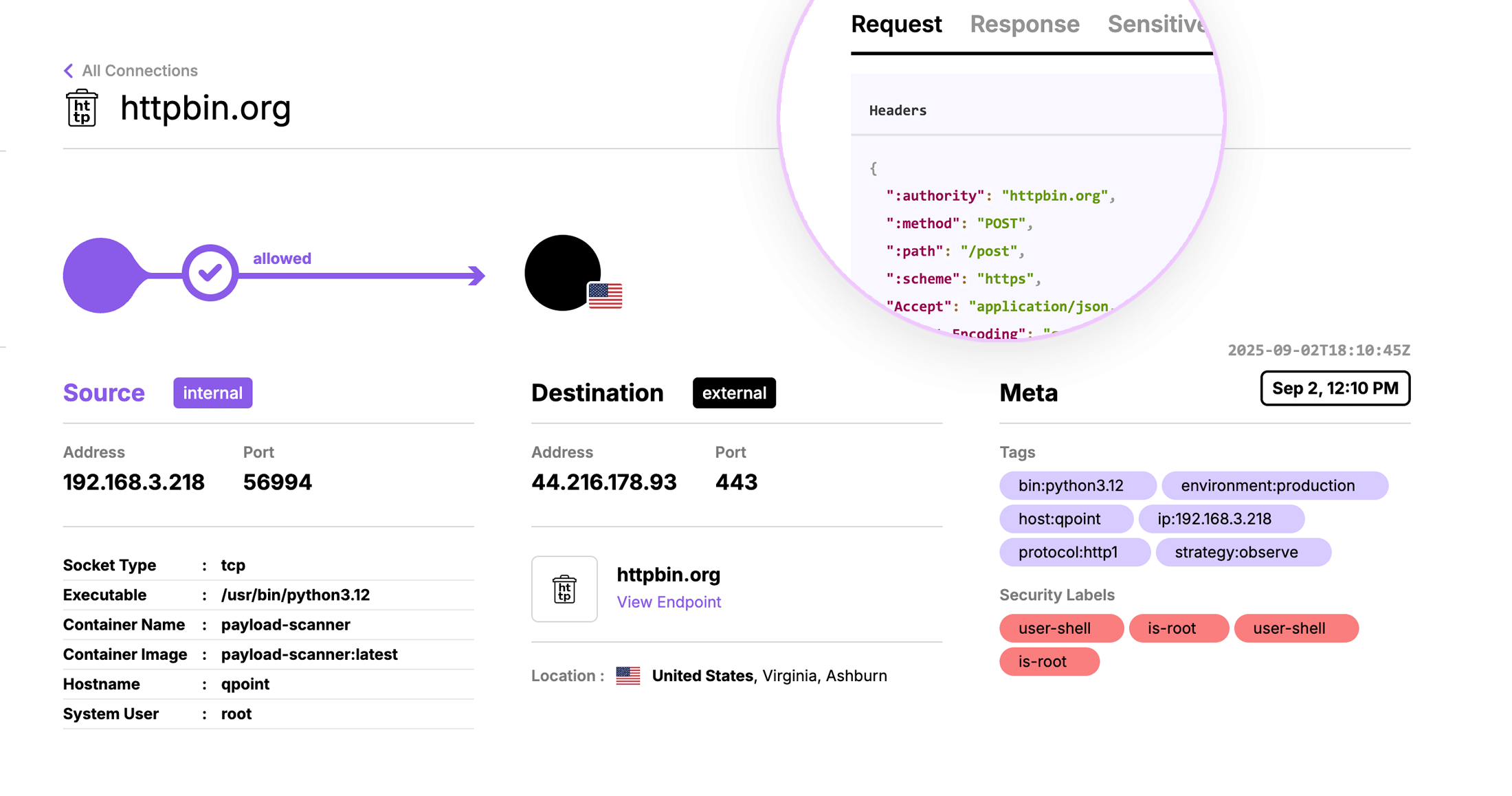
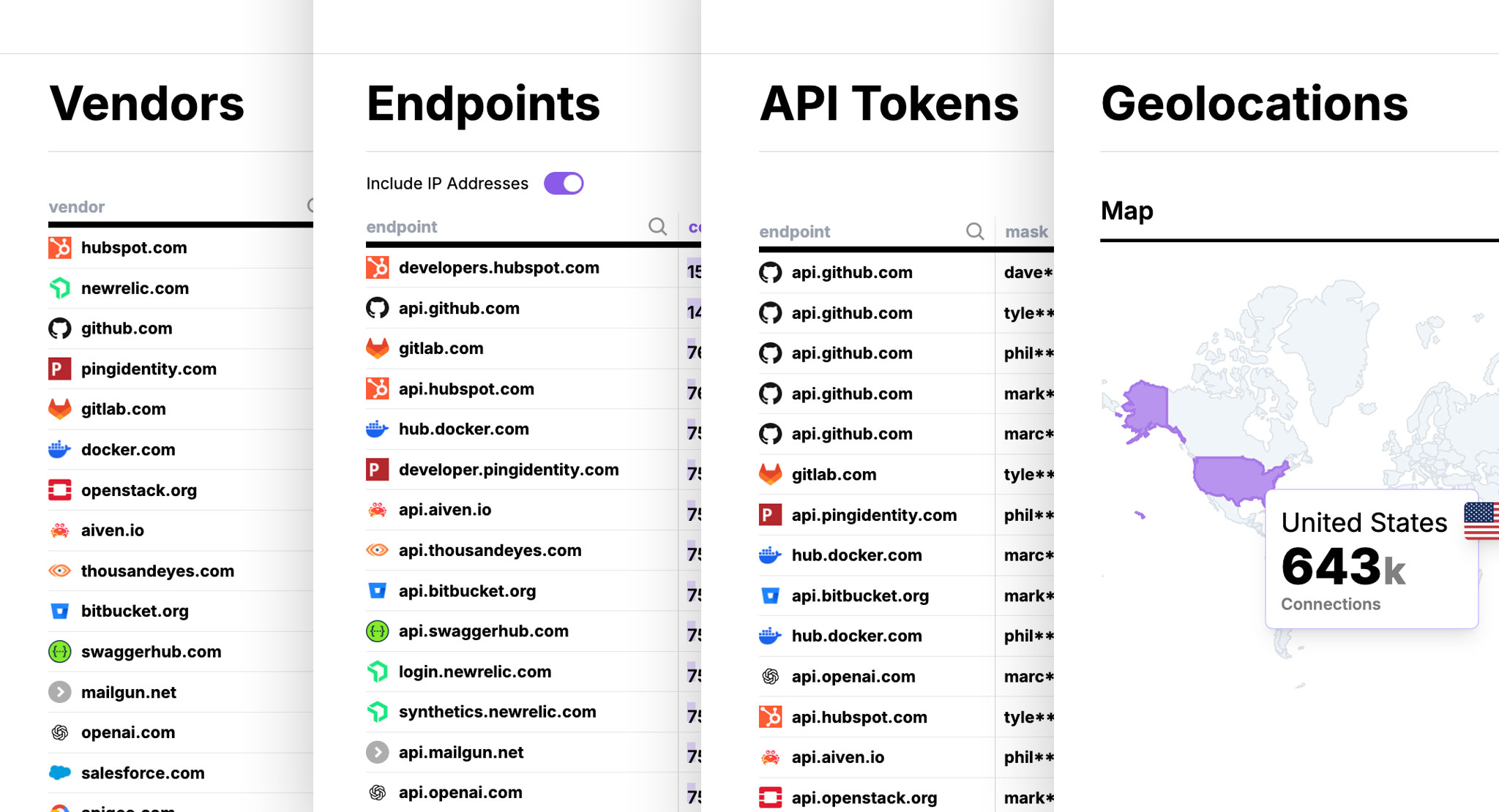
Illuminate Your Entire Network
Get a real-time, searchable inventory of every data flow—source, destination, and data classification.
Core Use Cases
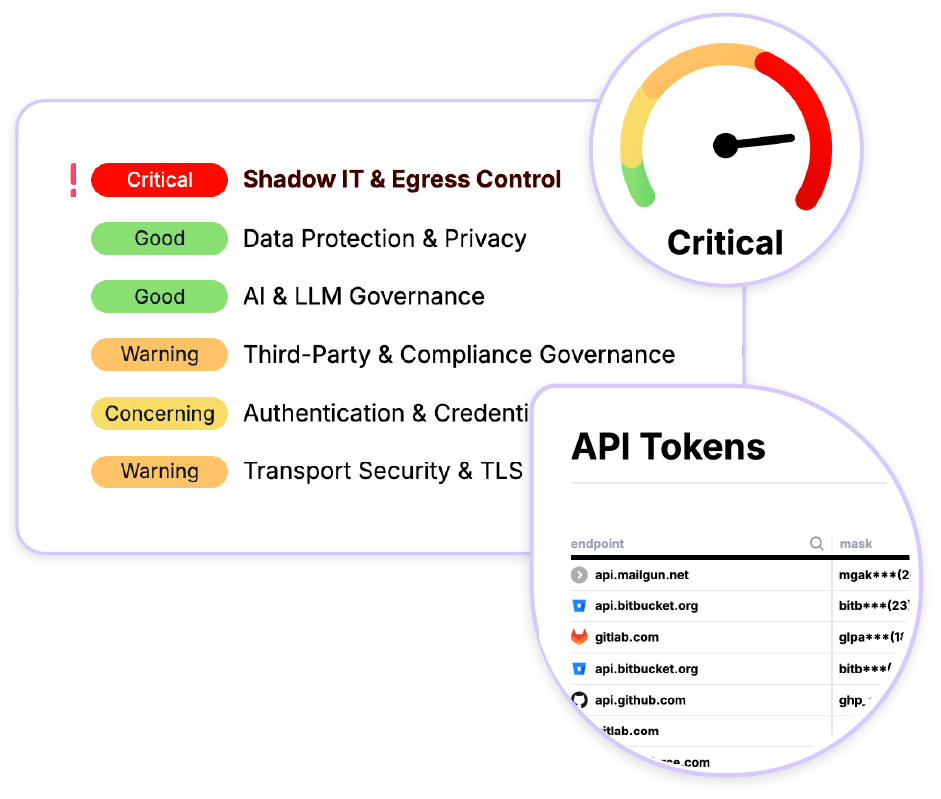
Expose and Quantify Third-Party Data Risk
See exactly what sensitive data you're sending to vendors.

Uncover Sensitive Data Exposure to AI
Gain visibility into what your teams are sending to external AI APIs..
Automate Data-in-Motion Evidence for Compliance
Pass audits with push-button simplicity by generating definitive proof of data residency.
Key Differentiators
Instant Visibility
Unmatched visibility from the ultimate source of truth. No blind spots.
Frictionless by Design
Installs in minutes, not months. No architectural changes.
From Connection to Context
Move from knowing a connection exists to knowing what sensitive data is at risk.
Request a Demo
Ready to see QPoint in action? Schedule a personalized demo to explore how our platform can help you gain visibility into your encrypted traffic and automate compliance evidence collection.