Managing External Integrations in Production Environments

In today's fast-paced tech environment, production applications increasingly rely on specialized third-party services for a wide variety of functions, including:
- Monitoring and analytics
- Data storage and processing
- Payment processing
- Identity verification
- Customer Relationship Management (CRM)
- Continuous Integration / Continuous Deployment (CI/CD) processes
- Helpdesk and support services
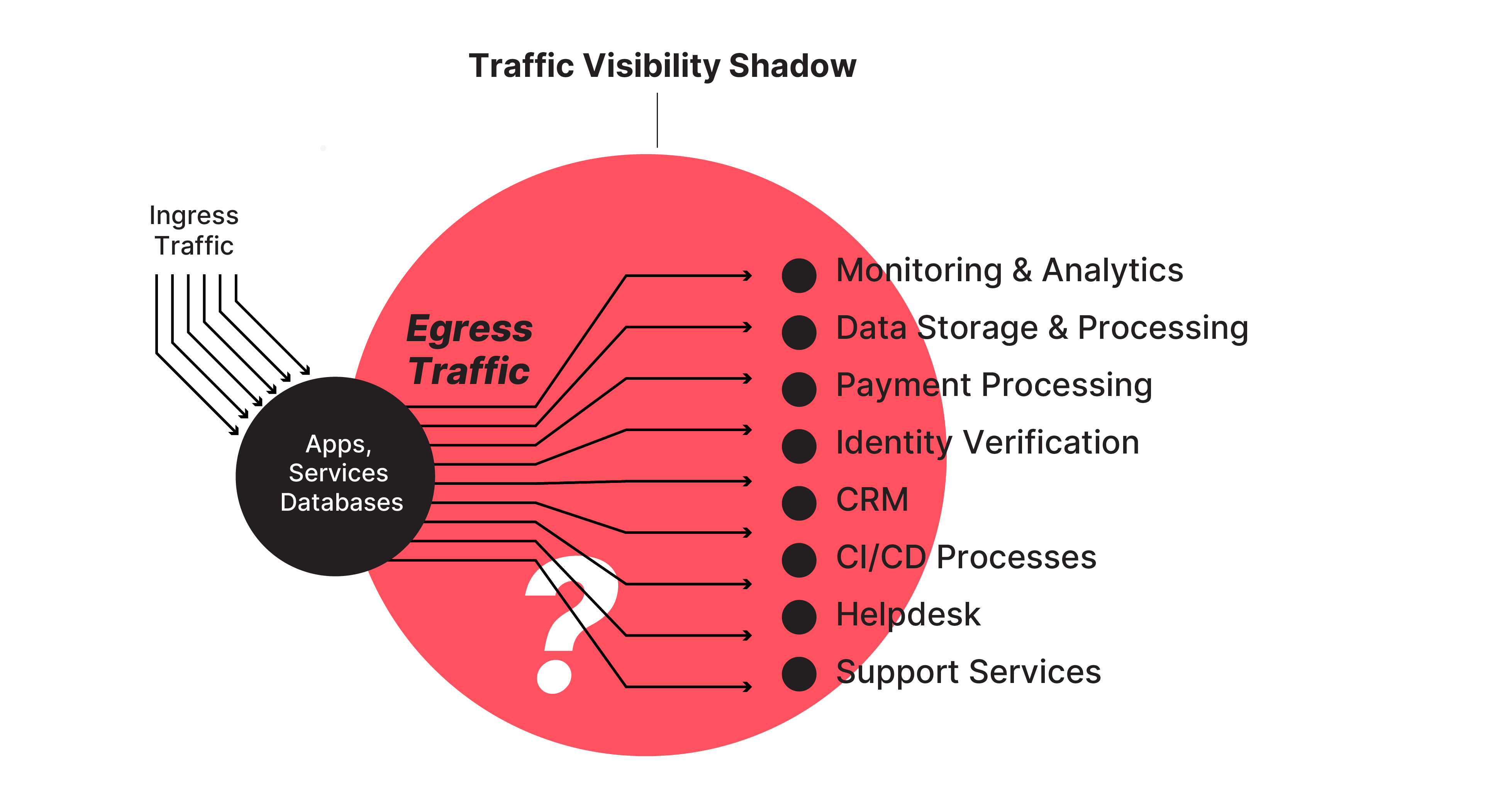
These dependencies require seamless integration, but platform teams are often hampered by limited visibility into and control over the egress traffic that flows from in-house applications to external dependencies and elsewhere. This gap can hide security risks, hinder compliance monitoring, and impede service interaction optimization.
A universal egress management offering like Qpoint provides the ideal toolset to observe, secure, and optimize these interactions, and tackle the associated risks head-on.
The following sections delve into the risks associated with overlooking egress observability and security in production environments and illustrate how Qpoint bridges this gap to foster a secure and resilient operational environment.
The Hidden Risks of External Service Integrations
The following risks and challenges can arise from inadequate management of your production applications' external dependencies:
- Lack of Awareness of Dependencies: The ignorance about which third parties your applications are liaising with crafts a shadow zone, paving the way for potential security risks. It also impedes swift incident resolution, turning issue source identification into a complex maze.
- Undetected Data Exfiltration: A blind eye to the type of data exiting your production environs could lead to unintended sharing of sensitive or regulated information. This unmonitored exfiltration can spell compliance violations, legal backlashes, and a tarnished reputation.
- Data Breaches: Feeble API security could invite unauthorized data access, culminating in data breaches, a financially and reputationally draining ordeal.
- Compliance Violations: The haze over API interactions can lead to non-compliance with regulatory mandates like GDPR or HIPAA, unfurling hefty fines and legal hassles.
- Operational Disruptions: Lax monitoring of third-party APIs’ uptime can trigger unexpected downtime, upsetting the operational rhythm. A vigilant monitoring system like Qpoint ensures real-time insight, enabling prompt actions to uphold operational continuity.
- Loss of Customer Trust: Security lapses and disrupted user experience can severely dent customer trust, driving them towards competitor shores.
Mitigating Risk with Egress Visibility and Control
Qpoint serves as an essential toolkit for platform teams and operators, offering unparalleled visibility and control over your external dependencies and traffic flows as well as defense against threats. By streamlining security and traffic management, Qpoint secures your digital resources and keeps your operations running smoothly. Here’s the breakdown:
Visibility and Control: Qpoint illuminates the once shadowy realm of third-party dependencies by categorizing API traffic, granting immediate access control. This transparency ensures that any abnormal interaction or security threat is detected and mitigated promptly.
Operational Resilience: Qpoint's vigilant monitoring of API uptime preemptively addresses potential downtime issues. The system's ability to function as a dynamic load balancer and traffic rerouter minimizes operational disruptions, thereby maintaining operational rhythm.
Data Exfiltration Guard: With Qpoint's advanced rule engine, your HTTP traffic is not just redirected but inspected. Headers and payloads are scrutinized, ensuring that no sensitive data leaves your network without explicit permission, maintaining compliance and protecting your reputation.
Compliance Assurance: Real-time alerts and comprehensive logging are more than just informational tools; they're the backbone of compliance. Integration with existing incident management systems ensures that every API interaction is logged, traceable, and aligned with GDPR, HIPAA, or other regulatory frameworks.
Trust Reinforcement: By safeguarding against security lapses and ensuring an uninterrupted user experience, Qpoint helps reinforce customer trust. Clients rest easy knowing that their service providers employ state-of-the-art API management solutions.
Conclusion
In the current climate of digital threats and stringent compliance requirements, Qpoint stands out as a pivotal solution for organizations aiming to protect and streamline their API-driven interactions. By choosing Qpoint, businesses can focus on growth and innovation, leaving the complexities of egress-related security in the hands of a capable, sophisticated system designed to address the complexities of today’s interconnected applications and platforms.
Are you interested in unparalleled visibility into and control over the egress traffic from your core applications to improve the reliability of your platform?
Explore how Qpoint can enable your team to enhance observability, increase operational resilience, and lock down your external traffic with a zero trust approach.