Uncovering the Hidden Footprint of Your Third-Party API Integrations

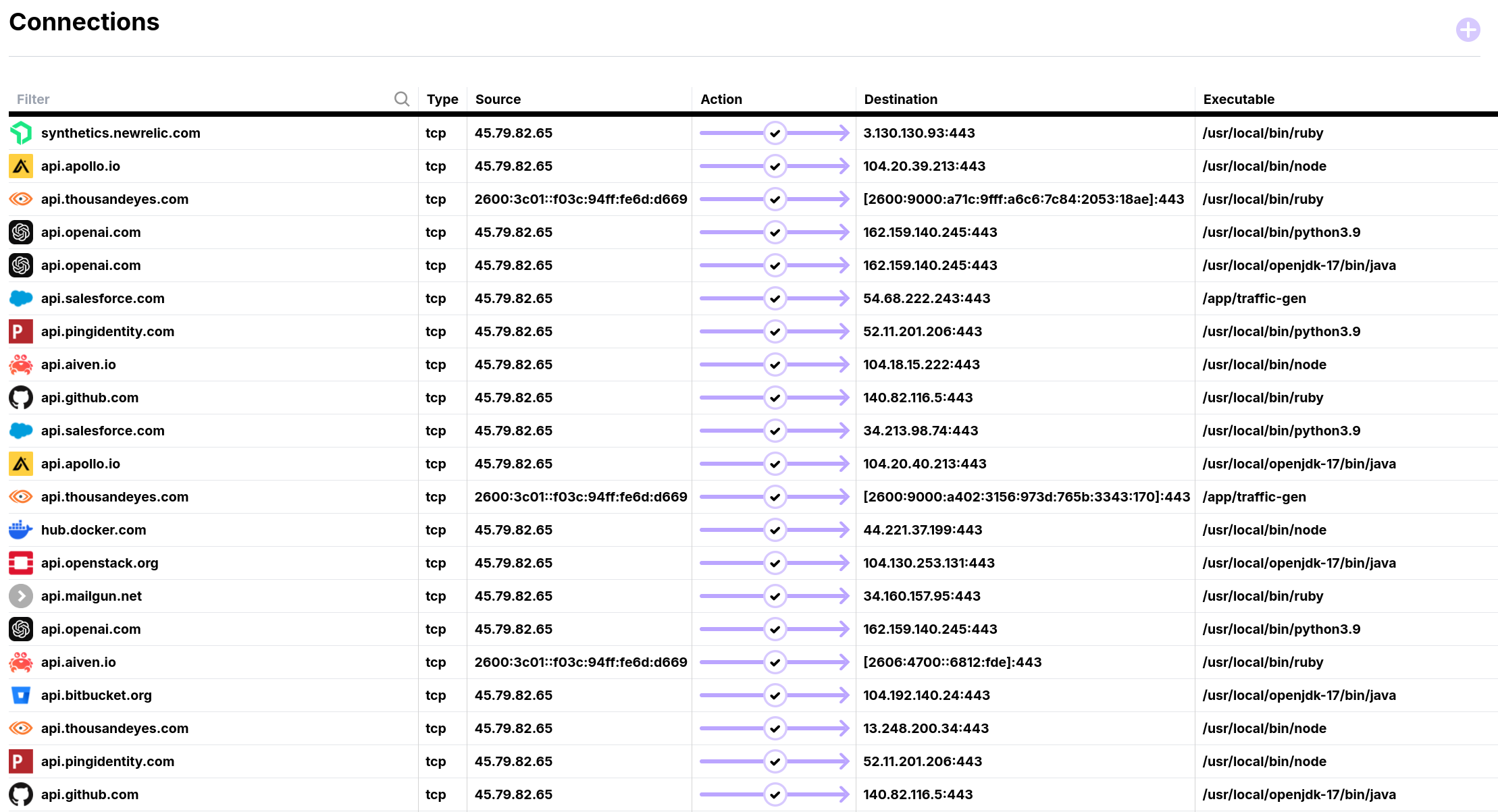
"Our API footprint is pretty simple - just a handful of core integrations." This common perception among engineering teams is understandable. Most organizations carefully track their business-critical integrations and maintain detailed documentation for their known third-party dependencies. But when teams gain true visibility into their production systems' HTTPS communications, reality often tells a different story.
The Great Discovery
When organizations first deploy comprehensive API monitoring across their environments, the results are often eye-opening. Dashboards light up with dozens, sometimes hundreds, of previously invisible HTTPS endpoints. "We had no idea we were making API calls to all of these services" is a common reaction. This revelation isn't unique to any particular company or team size—it's a pattern we've observed consistently across the industry, from small startups to large enterprises.
Let's break down what teams typically discover when they get full visibility into their HTTPS traffic:
1. Observability APIs
APM Services
- Multiple New Relic API endpoints (collector.newrelic.com, metric-api.newrelic.com)
- Datadog API calls (api.datadoghq.com, intake.logs.datadoghq.com)
- Dynatrace API endpoints for different telemetry types
Error Tracking
- Sentry.io API endpoints for error reporting
- Exception handling webhook endpoints
Logging Services
- Splunk HTTP Event Collector endpoints
- Elasticsearch API endpoints
- LogDNA/Mezmo ingestion APIs
Metrics APIs
- Prometheus remote write API endpoints
- Custom metrics aggregation APIs
- Cloud provider metrics APIs
2. Cloud Provider APIs
AWS Services
- Systems Manager API (ssm.us-west-2.amazonaws.com)
- ECR API endpoints for container pulls
- S3 API endpoints for object storage
- STS endpoints for token refresh
Event Streaming
- Confluent Cloud API endpoints (api.confluent.cloud)
- Schema registry API calls
- Kafka REST proxy endpoints
GCP Services
- Container Registry APIs
- Cloud Storage APIs
- Service account credential APIs
Azure Services
- Azure Container Registry endpoints
- Blob Storage APIs
- Key Vault APIs
3. Security and Compliance APIs
Vulnerability Scanning
- Snyk API endpoints for dependency scanning
- Rapid7 InsightVM API endpoints (insight.rapid7.com)
- Security scanner update APIs
CVE database sync endpoints
Certificate Services
- Let's Encrypt ACME protocol endpoints
- Certificate authority API endpoints
Security Tools
- Cloudflare API endpoints
- WAF configuration APIs
- Threat intelligence feed APIs
4. Development Infrastructure
Package Management
- npm registry API calls (registry.npmjs.org)
- PyPI API endpoints (pypi.org)
- Maven repository APIs
Version Control
- GitHub API calls (api.github.com)
- GitLab API endpoints
- Bitbucket API calls
CI/CD Systems
- Jenkins API endpoints
- CircleCI API calls
- Docker Hub API endpoints
Feature Management
- LaunchDarkly API endpoints (app.launchdarkly.com)
- Unleash feature flag APIs (unleash-hosted.com)
- Split.io API endpoints
5. Business and Product Integration APIs
Authentication
- Okta API endpoints (your-domain.okta.com)
- Auth0 authentication APIs
- SAML identity provider endpoints
Communication Services
- SendGrid API endpoints (api.sendgrid.com)
- Twilio API calls
- Slack webhook endpoints
Product Analytics
- Segment API calls
- Amplitude data collection endpoints
- Mixpanel event APIs
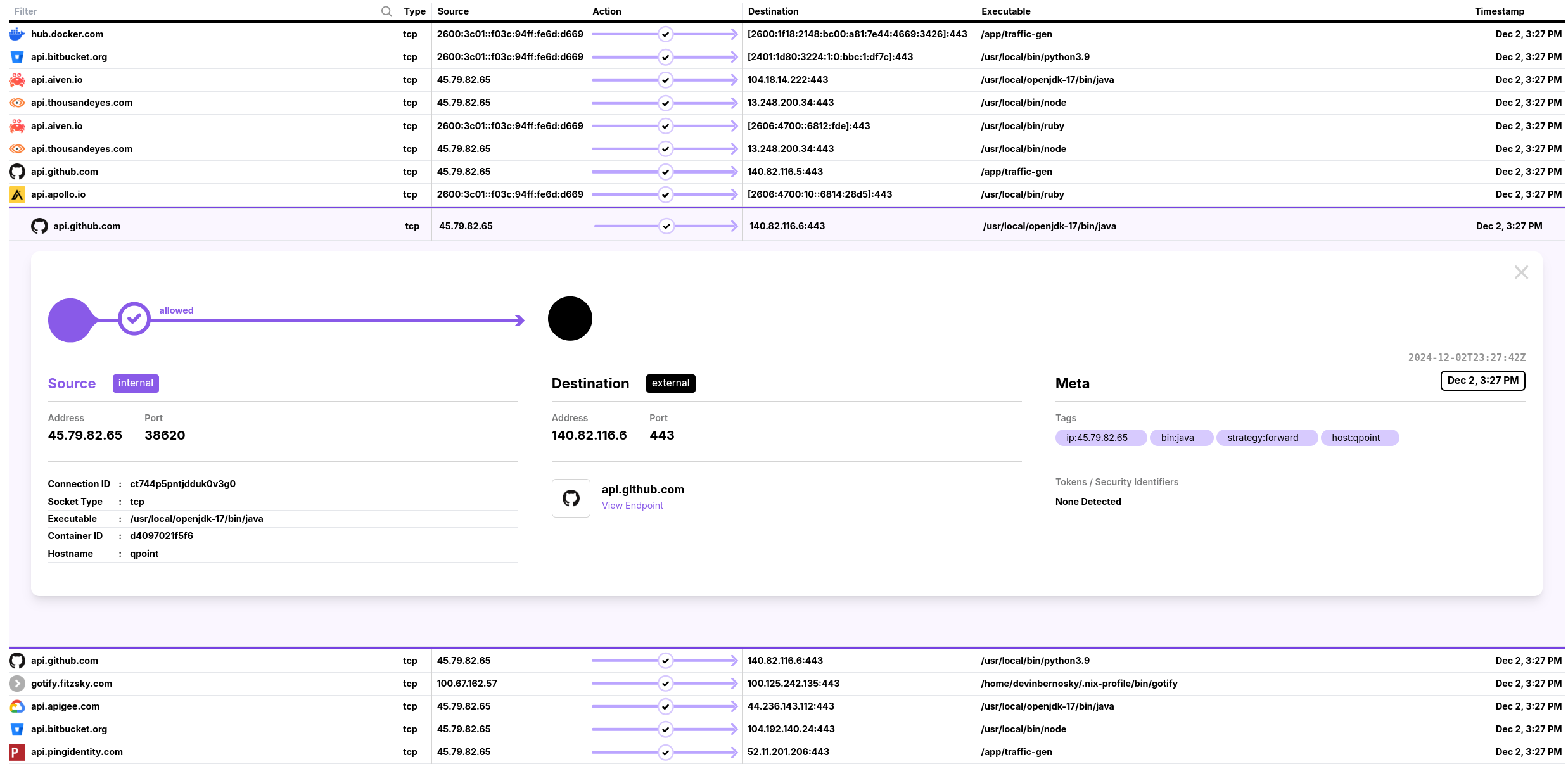
Why API Discovery Matters
The sprawling landscape of HTTPS integrations in modern organizations presents several critical challenges that can't be ignored. First and foremost is the security risk - each API endpoint your systems communicate with represents a potential vector for data exfiltration or compromise. This risk is compounded by the fact that many teams don't have a complete picture of their API footprint, making it impossible to properly secure all communication channels.
Cost implications also loom large in this landscape. Many third-party APIs operate on usage-based billing models, and without proper visibility, costs can spiral unexpectedly. Teams often discover they're paying for redundant services or inefficient API usage patterns that could be optimized with proper oversight.
Rate limiting presents another significant challenge. Modern applications often hit API rate limits unexpectedly, leading to service disruptions. These issues typically emerge from a lack of visibility into the aggregate API call patterns across different services and teams. What seems like reasonable API usage from one team's perspective might contribute to systemic issues when combined with calls from other parts of the organization.
Data privacy concerns are equally pressing. Without proper monitoring, sensitive data might be shared with third-party APIs without appropriate oversight or controls. This is particularly crucial in industries with strict regulatory requirements, where unauthorized data sharing could lead to compliance violations.
Finally, each API integration represents a potential point of failure in your system. The more integrations you have, the more complex your dependency chain becomes, and the harder it is to maintain reliable service levels.
Common Surprises in API Discovery
When teams first gain visibility into their API landscape, several common patterns emerge that often surprise even experienced platform teams. Abandoned API integrations frequently come to light during discovery exercises. These are endpoints that were supposed to be deprecated but continue to receive calls from legacy systems or forgotten integration points. These zombie integrations often consume resources and present security risks without providing any business value.
Perhaps most concerning is the discovery of development or testing APIs still being called from production environments. These might include sandbox environments, test endpoints, or staging APIs that should never be accessed by production systems. Such connections can pose significant security risks and may indicate gaps in deployment processes.
Teams also commonly uncover unexpected API usage patterns that warrant optimization. These include high-frequency health check calls that could be tuned, redundant API calls fetching the same data from multiple services, and chatty API patterns that could be batched for better efficiency.
Taking Action on API Discovery
Armed with visibility into your API landscape, several concrete steps can help bring order to the chaos. Begin with a comprehensive audit and rationalization effort. This involves mapping all API endpoints and their purposes, identifying redundant or unnecessary calls, and consolidating similar integrations where possible. The goal isn't just to document what exists, but to understand why each integration is necessary and whether it's being used effectively.
Optimization represents the next crucial phase. Look for opportunities to implement API call caching where appropriate, especially for frequently requested data that doesn't need to be real-time. Consider batching API calls to reduce network overhead and implement more efficient polling strategies. Often, simple changes to API call patterns can significantly reduce both costs and system load.
Security measures should be implemented systematically across all discovered endpoints. This includes ensuring proper API authentication mechanisms are in place, monitoring for sensitive data in API payloads, and enforcing TLS best practices. Pay particular attention to endpoints that handle sensitive data or provide access to critical systems.
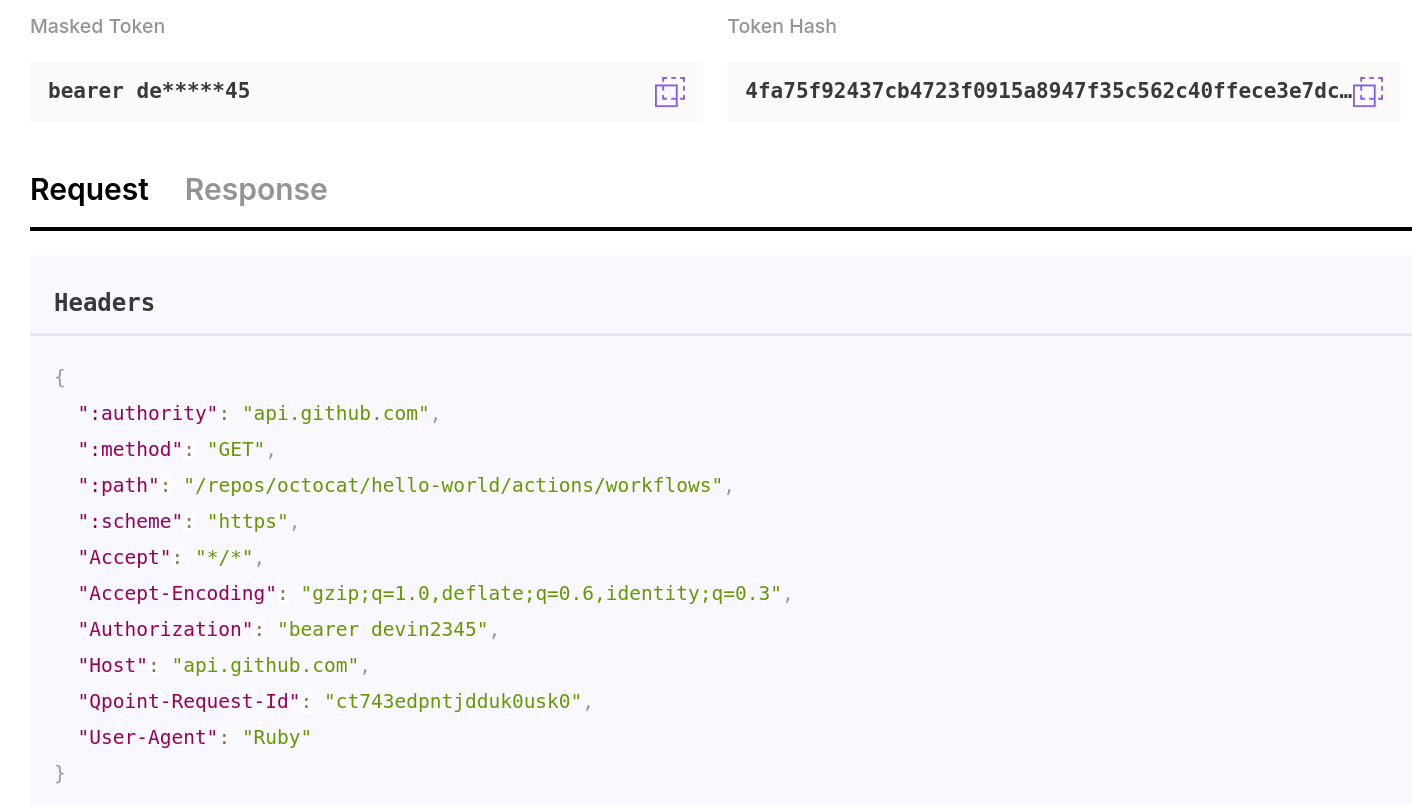
Finally, implement robust cost control measures. This goes beyond simple monitoring - track API call volumes and patterns to identify opportunities for optimization. Look for ways to reduce unnecessary API calls and optimize usage tiers across services. Consider implementing API quotas or alerts to prevent unexpected cost overruns.
The key to success in managing your API landscape is maintaining continuous visibility. Regular audits and monitoring help ensure that new integrations follow established best practices and that existing integrations continue to serve their intended purposes efficiently and securely.
Qpoint Makes API Discovery and Monitoring Easy
The reality is that modern production systems make far more API calls than we typically realize. The first step to managing this complexity is understanding it. Tools like Qpoint that provide automatic discovery and continuous monitoring of HTTPS traffic are becoming essential for maintaining secure, efficient, and compliant systems.
Remember: you can't secure what you can't see, and you can't optimize what you don't measure. The true scope of your API integrations might surprise you—but knowing is the first step to improving.
Ready to experience the Qpoint difference? Try now for free or schedule a demo today and see how Qpoint can transform the way your ops team manages its applications’ third-party dependencies and external traffic flows.