Why Securing Egress Traffic Matters

Thousands of data breaches occur in the U.S. every year, costing companies close to a whopping $10 million per breach. While countless tools and vendors aim to reduce the number and impact of these breaches, the reality remains that they continue to grow. This is due in part to the fact that many solutions are focused on what (or who) is entering the network, but remain blind to what is exiting it. Modern production applications are increasingly reliant on a web of external vendors and APIs, resulting in egress traffic that exposes the organization to as much risk as ingress traffic does.
Egress vs. Ingress
Egress traffic refers to the data that flows out from a particular network or device to another network, such as the internet or a different local network. It can include various types of data, such as web requests, emails, file downloads and more. Ingress traffic is the opposite of egress traffic. It refers to the data that flows into a particular network or device from another network. Understanding and managing both types of traffic is essential to ensure efficient network operation and security, but many companies have a blind spot when it comes to egress. Over the years, this has contributed to massive data breaches that could have been mitigated with better visibility into, and control over, egress.
Mitigating Data Breaches with Observability and Zero Trust
Regardless of an attacker’s strategy, a cyber attack must exfiltrate sensitive data to be successful. For the vast majority of attacks, a tool that can restrict outbound access based on identity or scan for sensitive data on egress can prevent or significantly reduce the impact of a data breach. There have been numerous breaches over the last decade that could have been mitigated with a zero trust strategy for egress, including the following that resulted in long-lasting reputational damage.
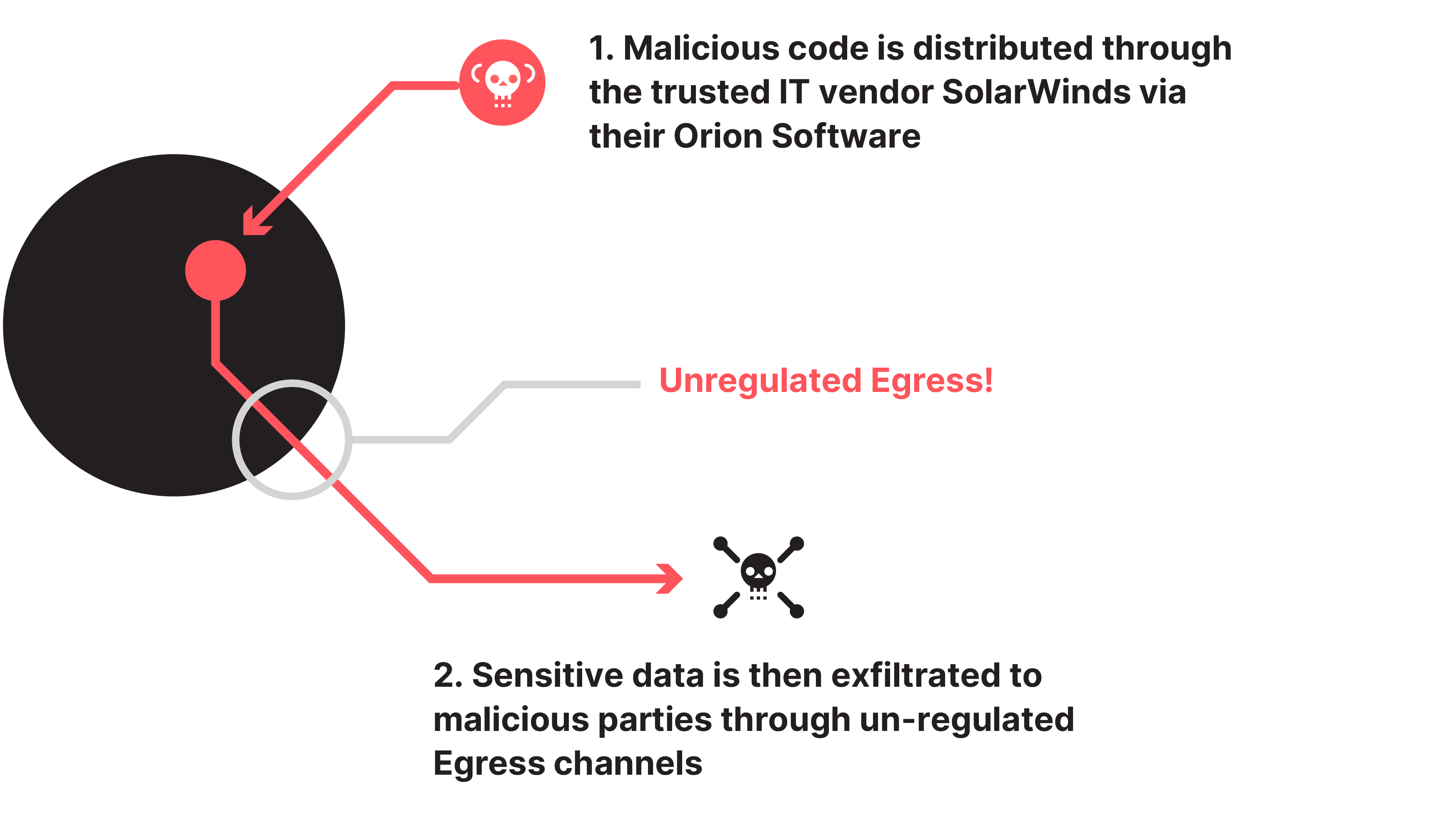
SolarWinds Orion
This 2020 attack involved the insertion of malicious code into SolarWinds' Orion IT management software, which was distributed to thousands of SolarWinds customers through software updates. While the breach was not solely due to poor egress security, implementing egress best practices could have mitigated its impact and prevented aspects of the attack. For example, if the affected networks had a tool controlling which external APIs SolarWinds could access, it might have prevented the malware from communicating with the attacker's servers.
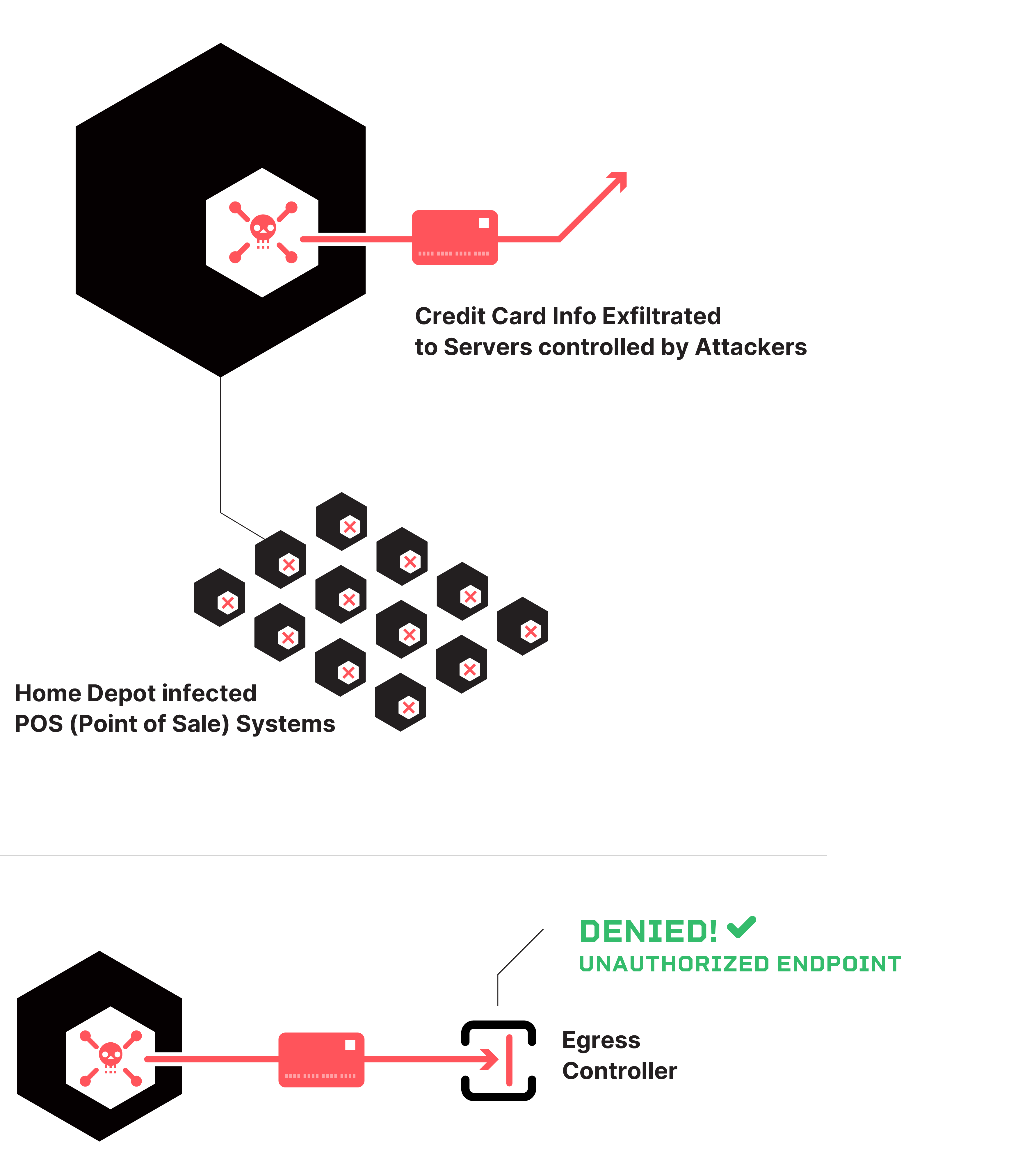
Home Depot
In 2014, customer credit card information was exfiltrated from Home Depot point-of-sale (POS) systems to external servers controlled by attackers. If Home Depot’s team had better visibility into the egress traffic from individual store locations, they may have been able to identify the compromised POS systems and the extent of the breach faster. A zero trust strategy designed to limit external access from Home Depot's store location networks and enforced by an egress controller could have prevented access to the attacker's external systems altogether.
Implementing a zero trust strategy for egress has become even more critical in recent years as attackers have gotten more sophisticated and attack vectors have significantly increased. Organizations can reduce or eliminate the impact of cyber attacks by deploying tools that increase visibility, restrict outbound access, and scan for sensitive data on egress - as evidenced by the above high-profile breaches and many more like them.
Egress Security Best Practices
The following best practices set the foundation for egress security for a platform engineering team. By implementing these practices, organizations can greatly reduce the risk of an egress-related data breach.
- **Discovery & Monitoring: **By tapping into their egress traffic flow, platform teams can discover which applications are making external requests and what the endpoints are. This is vital for understanding the full scope of external dependencies and interactions, and detection of anomalies in traffic patterns.
- **Alerting: **Alerts can notify the team of a potential issue or anomalous behavior before it escalates into a major problem. This proactive detection can minimize downtime and maintain the stability of the platform.
- Audit Logging: Maintaining detailed audit logs of egress traffic is crucial for tracking all outbound requests and responses. This ensures traceability and accountability, facilitating thorough investigations in case of security incidents.
- Access Control: A zero trust approach with default deny and identity-based access control policies ensures that only authorized applications have the necessary permissions to access external resources. This reduces the likelihood of sensitive data exfiltration by restricting external access to only those applications that require it.
- API Token Visibility: Getting a handle on API token sprawl reduces the risk of unauthorized access, data breaches and data exfiltration by hackers using stolen credentials. By implementing robust management, monitoring and governance practices, organizations can ensure the secure use of API tokens across environments.
- **PII Mapping & Scrubbing: **A platform team needs to know which applications are sending PII outside the network and where it’s going, in order to prevent unauthorized exfiltration of sensitive data. The ability to obscure or scrub sensitive data in-line before a request leaves the network provides extra insurance.
Tap In and Take Control of Egress with Qpoint
Visibility into and control over egress traffic is an indispensable part of a platform team’s security strategy as core production applications become more interconnected and as attackers grow more sophisticated. Implementing the above best practices with home grown tooling, however, can be a challenging task and a significant distraction for busy engineers.
Qpoint offers an easy to deploy and flexible solution to enable platform teams to enhance egress observability, apply zero trust security principles, and increase operational resilience for the platform as a whole and the core production applications that run on their networks.
Are you ready to safeguard egress for your production application environments? Explore how Qpoint can help you tap into and take control of your egress traffic in our docs or with a demo by our solutions engineering team.