OG Image Preview
Preview how social media sharing images will appear for all blog posts and case studies.

What Your AI Assistant Can't See (And How to Fix It)
Your AI coding assistant can read every line of your code. But when that code makes an HTTP request, your AI has no idea what comes back. Here's how to give it eyes on live network traffic.

Introducing DevTools: Chrome-style Network Tab for Your Linux Server
We built a browser-based debugging tool that shows live http/s traffic on production servers. No proxies, no certificates, no code changes. Just the visibility we always wished we had.


The Heisenberg Horror: Why Debugging Tools Make Bugs Disappear
Production bugs that vanish when you try to debug them. Learn why traditional debugging tools change what they observe and how to catch Heisenbugs with unmatched visibility.

Built to Integrate: Why Qpoint's Modular Architecture Matters
Most security vendors force you into all-or-nothing adoption. Learn why Qpoint's modular architecture (QTap, QPlane, QScan) gives you unmatched visibility with complete flexibility over data storage, deployment, and integration.

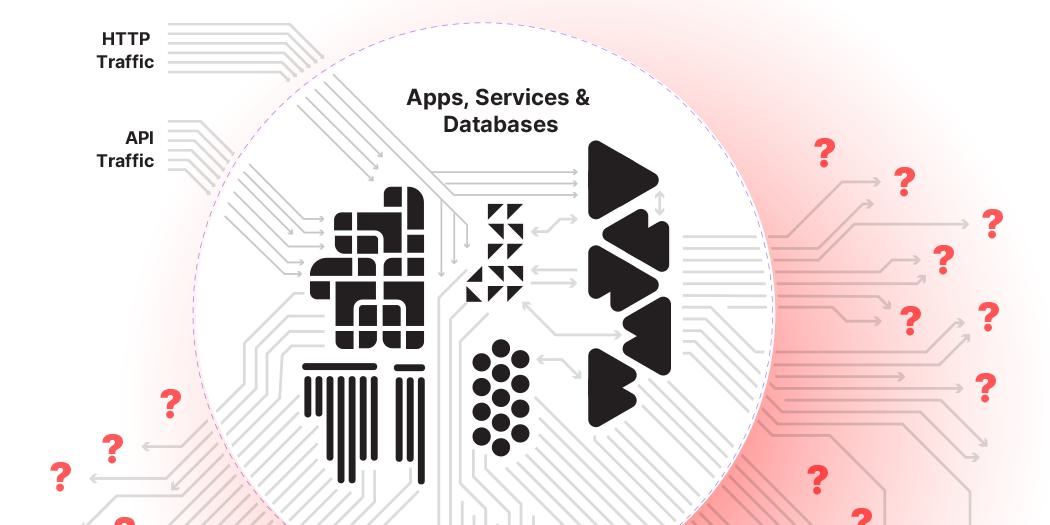
Are You Watching What's Leaving Your Network?
Business units are racing to integrate AI, creating a massive encrypted blind spot in outbound API calls. Learn how to gain visibility into what data is being sent to external AI services without disrupting your applications.

The Hidden Complexity of External Dependencies - How Qpoint Solves a Cloud-scale Problem
Your system is only as reliable as its weakest dependency. Learn how external service failures impact cloud-scale systems and how Qpoint provides immediate visibility into third-party dependencies without code changes.

The CISO's Checklist - What Your Current Tools Can't Tell You
As a CISO, you've invested heavily in security tools. Yet when the board asks about your organization's true risk exposure, you still face uncomfortable silence around critical questions. The problem lies in what encryption hides from your existing security stack.

The M&A Due Diligence Black Box: Why Technical DD Takes Weeks (And How to Get It Done in Days)
Every CISO that's ever gone through an acquisition knows the technical due diligence black hole. Learn how simple visibility can transform weeks-long technical DD into a days-long observational exercise.

How eBPF-Based Egress Monitoring Would Have Caught the Shai-Hulud npm Worm in Real-Time
September 2025 marked a watershed moment for supply chain security when the Shai-Hulud worm became the first self-replicating malware to propagate through the npm ecosystem. This post examines how Qpoint's eBPF-based data-in-motion security would have detected this attack at the moment of compromise.


The Encryption Paradox
Every security incident post-mortem reveals the same pattern: the evidence was there in the network traffic all along. The warning signs existed, but they were hidden beneath layers of encryption and distributed across dozens of services.


Why Running Qtap in Production is Safe - A Deep Dive into eBPF and Privilege Boundaries
Let's address the elephant in the room. After recent high-profile kernel agent failures that took down millions of systems worldwide, your security and operations teams are rightfully cautious about anything that touches the kernel. When we tell you that Qtap needs elevated privileges and deploys eBPF programs into kernel space, we understand the skepticism.

The eBPF Verifier - How Linux Safely Runs User Code in Kernel Space
Understanding how the Linux kernel can safely run user-supplied programs without risking system stability through eBPF's mathematical verification system.


The Impossible Proxy - An Egress Journey
We just need all external traffic to go through an egress proxy. That's how it always starts. A seemingly simple security requirement that sounds reasonable in the boardroom. The CISO nods. The compliance team is satisfied. The architecture review board approves. And then, someone has to actually build it.

Security Observability for the Encrypted Cloud
See through encryption to secure complex production cloud applications


A Story About Missing Context
Learn how a lack of visibility into external API calls can leave you flying blind during critical incidents. This story illustrates the challenges of debugging with fragmented logs and introduces a new approach to gain complete context for faster resolu


Qpoint Achieves SOC 2 Type II Compliance
Qpoint has achieved SOC 2 Type II compliance, demonstrating our commitment to security, privacy, and protecting customer data with independently validated controls and processes.

The Truth is on the Wire
By tapping into raw wire data, Qpoint can offer deep, actionable insights to help organizations troubleshoot and solve issues that traditional APM tools struggle to find.

New Year, New User Experience!
We sprinted to the finish line in 2024 to deliver a major update to our user interface and workflow.

The Hidden Risks of Third-Party API Dependencies
Discover the hidden risks of third-party API dependencies—from reliability challenges to hidden costs—and learn how Qpoint uses eBPF to provide the visibility and control that operators and SREs need.

Uncovering the Hidden Footprint of Your Third-Party API Integrations
Learn how Qpoint reveals your true third-party API footprint to boost platform reliability, control costs, and ensure compliance.

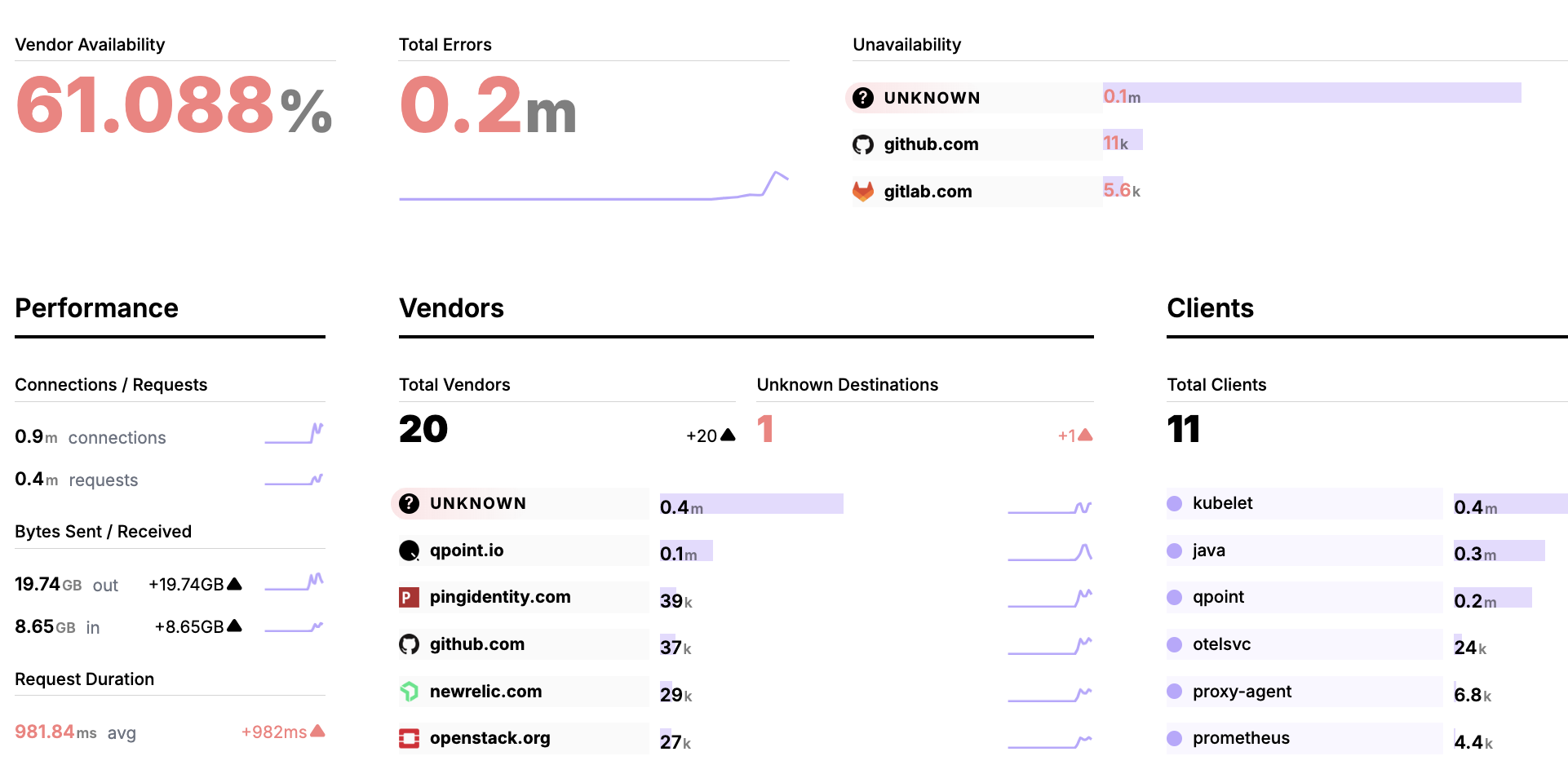
Turning Blind Spots Into Visibility and Insights for SRE Teams
Qpoint provides game-changing visibility into external service dependencies and third-party API traffic for ops teams looking to keep their production applications resilient, secure, and cost-effective.


Qpoint Closes Pre-Seed Funding and Launches eBPF-based Monitoring and Control for External APIs and Services
In line with Qpoint's announcement of pre-seed funding, it has also launched a new eBPF-based visibility and control platform to easily see and control external services.


What is eBPF?
Understand how eBPF technology works, its key use cases, and how it empowers teams to optimize application performance, enhance security, and troubleshoot faster.


What's the difference between my APM tool and eBPF-powered QPoint?
Qpoint is purpose-built to monitor & secure applications' external dependencies and traffic flows for smooth operations and protection against hidden outage risks.

Conquering the Hidden Challenges of External Service Integrations
Discover why implementing a traditional egress proxy is often impossible in modern microservices environments. Learn about the challenges and a new approach for visibility and control.

Lessons in Reliability: Rishi Goomar's Journey from Dev to SRE
Insights from a Staff SRE at Lattice on Building Resilient Systems

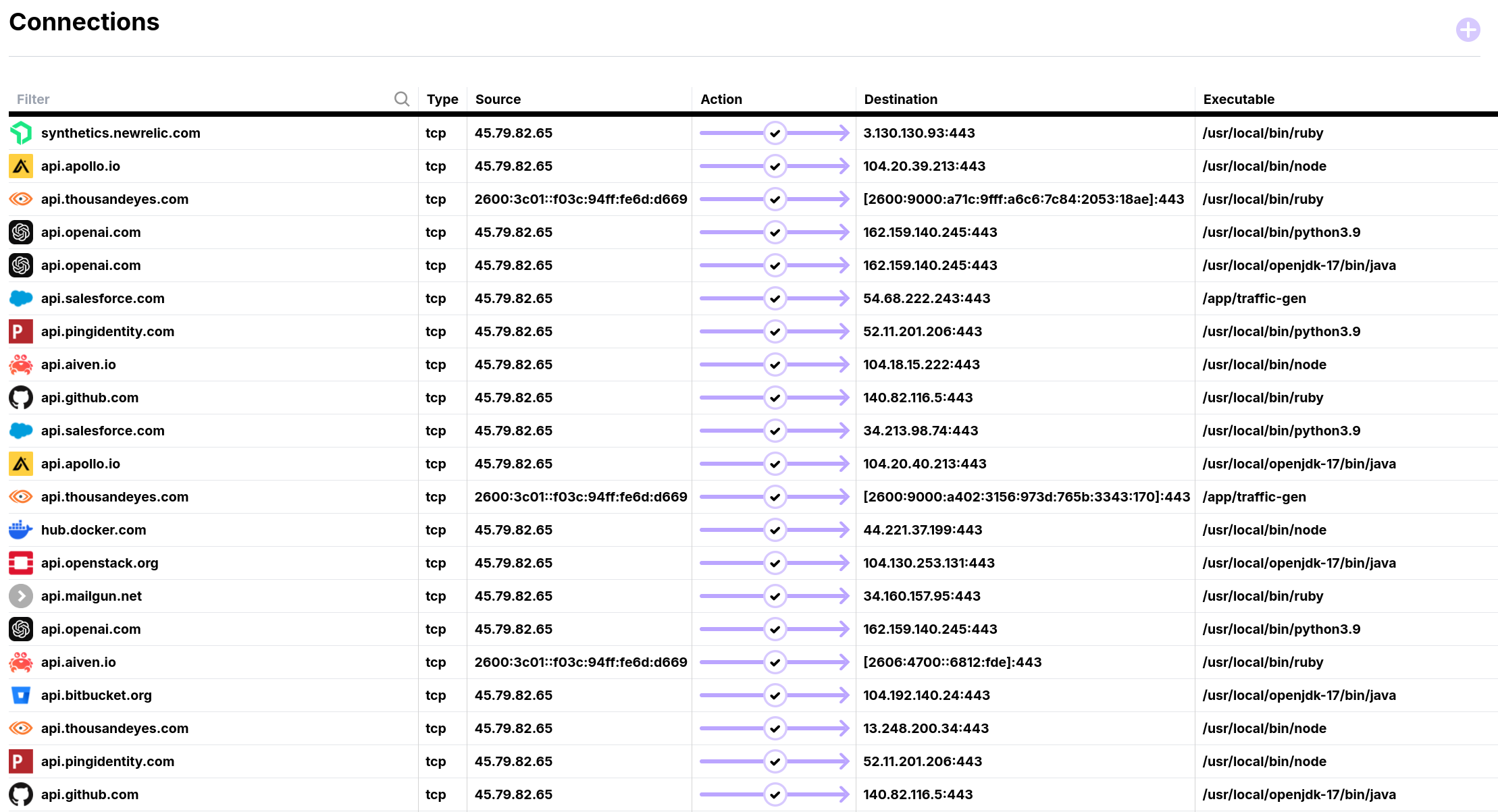
Tap Into Your External API Traffic with eBPF
Qpoint taps into connections at the source, enabling you to see through encryption, map your dependencies, and enforce egress controls

Managing External Integrations in Production Environments
External service Integrations and their hidden challenges are the new frontier for platform teams and operators.


Mitigating Software Supply Chain Risk with Qpoint
The modern software development paradigm enables rapid innovation, but developer reliance on third-party libraries, frameworks, and external services can introduce software supply chain risk as a result.


Improving Platform Reliability with Qpoint
Explore how operators and SREs can improve service reliability by leveraging Qpoint's comprehensive egress observability and monitoring solution.


Managing External API Dependency Risk
Discover how Qpoint can help operators manage third-party dependencies and increase operational resilience with a holistic approach to egress traffic observability and management.

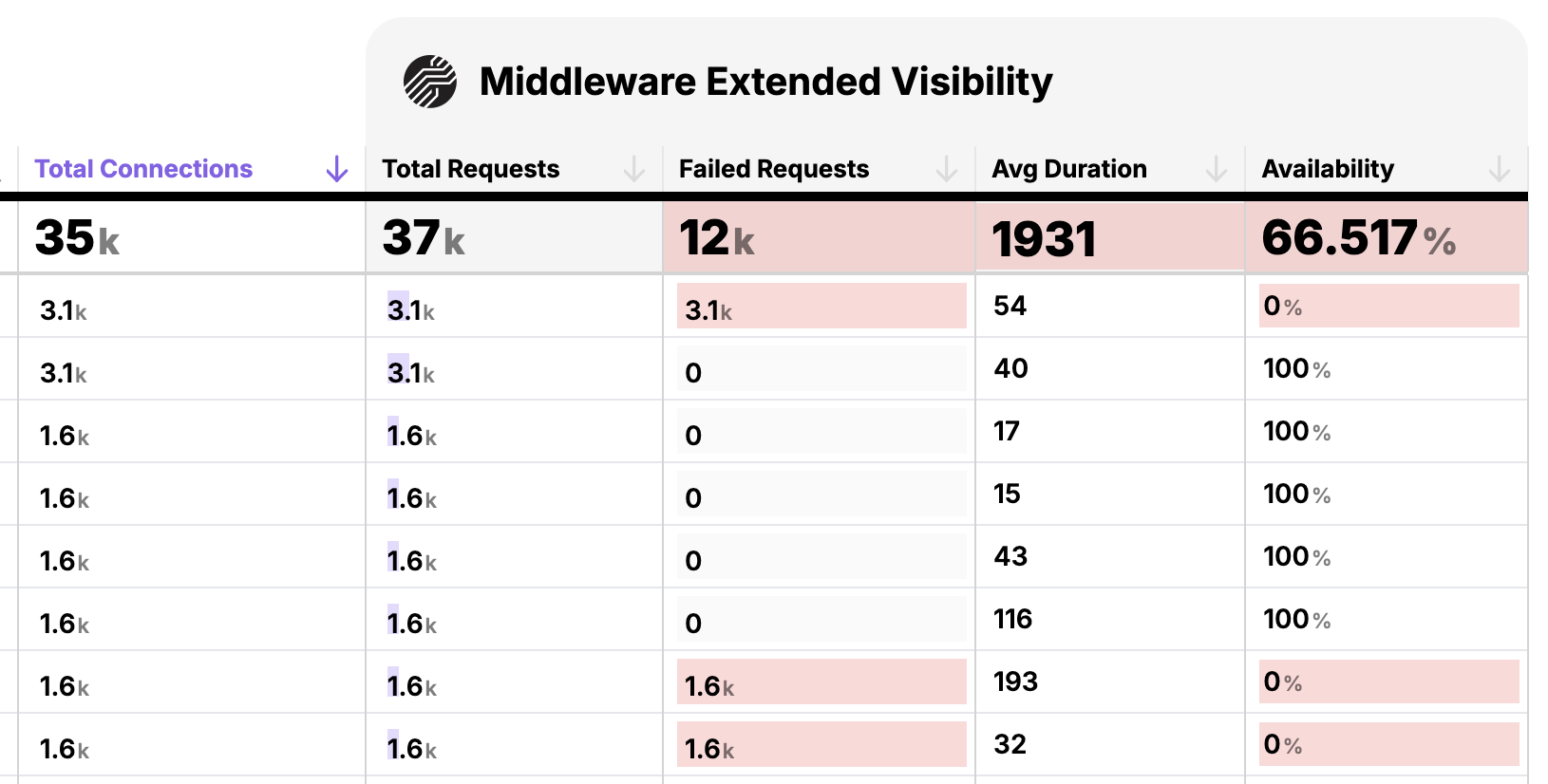
How We Use Middleware
Discover how Qpoint's versatile middleware subsystem empowers platform engineering teams with customizable traffic handling and advanced egress management capabilities.

Why Securing Egress Traffic Matters
Learn egress security best practices for production environments and the importance of securing egress traffic for preventing and mitigating data breaches.


Meeting Regulatory Compliance Requirements for Your External Integrations
This is Part 1 of our series on how platform teams can leverage Qpoint's visibility and control capabilities for external integrations to meet regulatory compliance requirements for their production environments.


Apollo.io Achieves Data-in-Motion Security with Qpoint
This is the definitive guide for growing companies grappling with complex external integrations. See how Apollo.io transformed operational chaos into unified DevSecOps bliss.